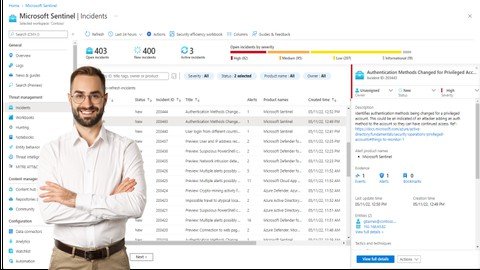
Free Download Microsoft Sentinel Seim Implementation & Automation Published 9/2023 MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz Language: English | Size: 734.41 MB | Duration: 1h 38m Empower Your Security Infrastructure with Next-Gen Cloud SEIM Expertise
Free Download Mastering Salesforce Associate Certification Published 9/2023 Created by Faisal Muhammad MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch Genre: eLearning | Language: English | Duration: 135 Lectures ( 7h 55m ) | Size: 5.65 GB
Free Download Intro to Windows Digital Forensics and Incident Response Published 9/2023 Created by Robert McMillen MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch Genre: eLearning | Language: English | Duration: 21 Lectures ( 2h 50m ) | Size: 1.1 GB

Free Download AWS Certified Cloud Practitioner (CLF–C02) Complete Course Published 9/2023 Created by Jason Dion • 1 Million+ Enrollments Worldwide,Dion Training Solutions • ATO for ITIL & PRINCE2,Dion Training Solutions • ATO for ITIL & PRINCE2,Jamario Kelly MP4 | Video: h264, 1280x720 |

Free Download Artificial Intelligence Foundations – Neural Networks (2023) Released: 09/2023 Duration: 1h 45m | .MP4 1280x720, 30 fps(r) | AAC, 48000 Hz, 2ch | 182 MB Level: Beginner | Genre: eLearning | Language: English An artificial neural network uses the human brain as inspiration for
Free Download Practical Pentesting Last updated 5/2023 Created by Stone River eLearning ITPROTV MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch Genre: eLearning | Language: English + srt | Duration: 21 Lectures ( 7h 19m ) | Size: 7.81 GB
Free Download GIAC Security Essentials (GSEC) Last updated 5/2023 Created by Stone River eLearning ITPROTV MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch Genre: eLearning | Language: English + srt | Duration: 34 Lectures ( 10h 44m ) | Size: 11.6 GB
Free Download Digital Forensics & Incident Response Pro Published 9/2023 Created by Aashir Masood MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch Genre: eLearning | Language: English | Duration: 18 Lectures ( 3h 36m ) | Size: 1.68 GB

Free Download DBMS Module – 5 Published 9/2023 Created by Prabh Kirpa Classes MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch Genre: eLearning | Language: English | Duration: 5 Lectures ( 1h 54m ) | Size: 2 GB
Free Download Secure Computer User by Yash Pandit Published 9/2023 Created by Yash Pandit MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch Genre: eLearning | Language: English | Duration: 16 Lectures ( 4h 51m ) | Size: 2.5 GB